Now, we will talk about other practices for information security: use 2-step verification, use genuine software, use customize installation, and don’t click on strange links/files.
5. Use 2-step Verification
Most of internet services provide 2-step verification. When you sign in to your account, the service will need you to enter a verification code from authenticator app or text message(sms) to verify it’s you. Such as Google provide two kinds of verification: 2-step verification and Google Authenticator
If you want to turn on Google 2-step verification, please follow Google Help center: Protect your account with 2-step verification
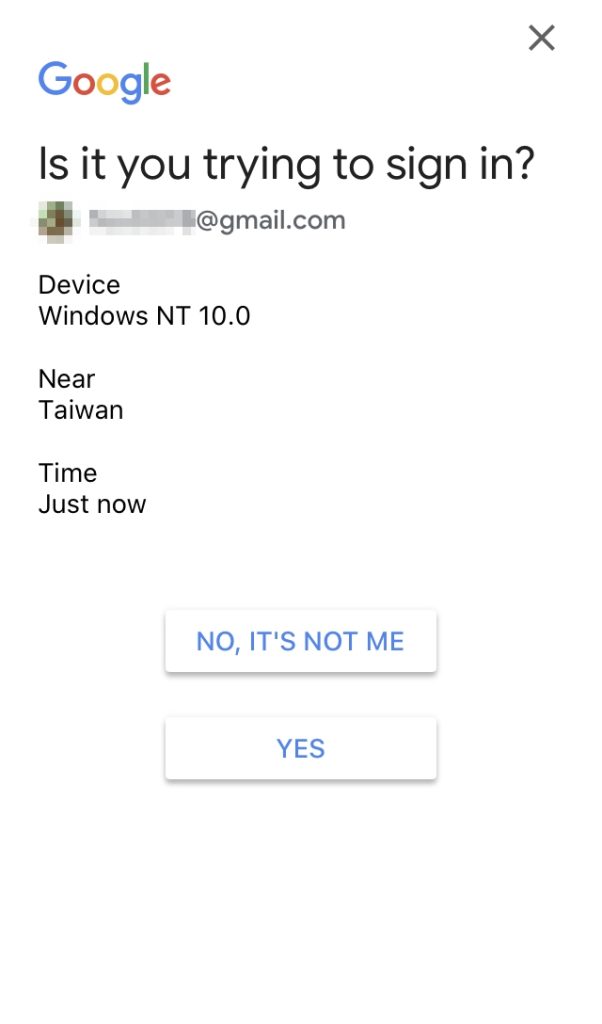
When you sign in to your account, google will send a notification to your gmail/google app on your device.

If you allow this sign in requested, tapped Yes on your device.
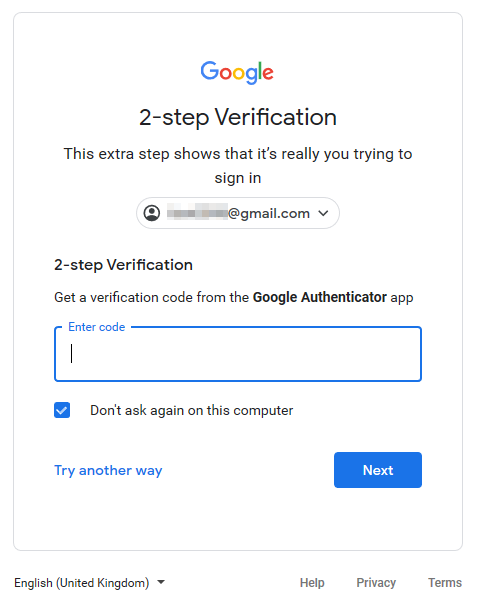
You also can use Google Authenticator, please follow: Get verification codes with Google Authenticator
When you sign in to your account, you will need to enter a verification code from the Google Authenticator app on your device.
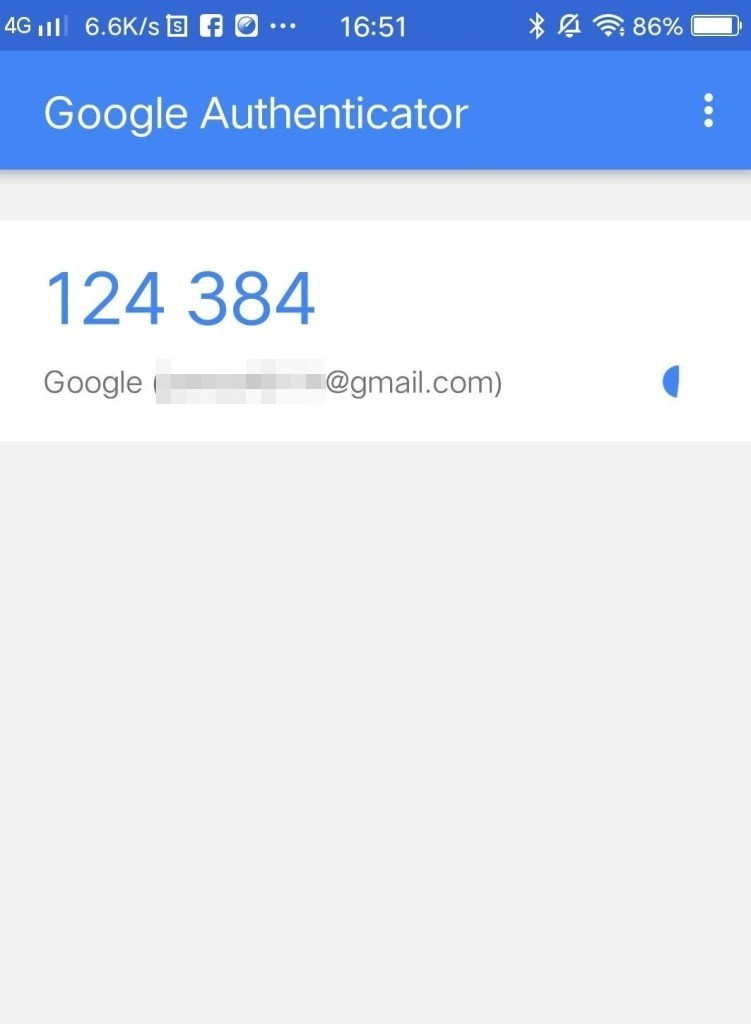
You can find the verification code on your device.
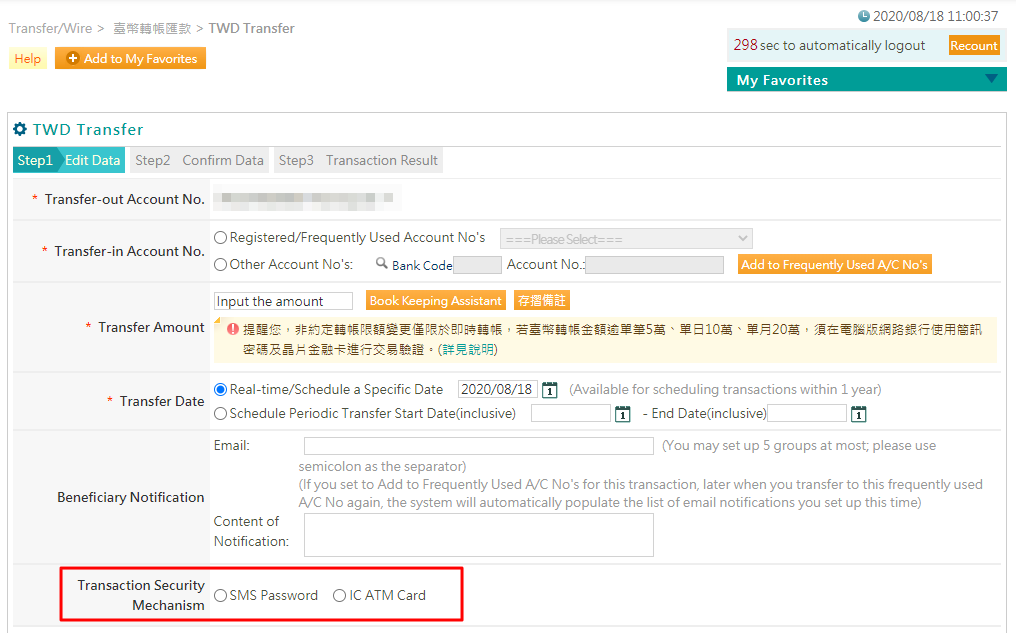
Also, Most of e-banks are using similar mechanism.
If you want to transfer money, you may use text message, ATM Card, or Authentication App to verify yourself.
6. Use genuine software, DO NOT using Unknown or illegal pirated software
You can’t figure out whether these pirated software will embedded virus such as Trojan. Besides, Pirated software can’t be updated. That’s means if any vulnerability be found out in this software, your device will at risk.
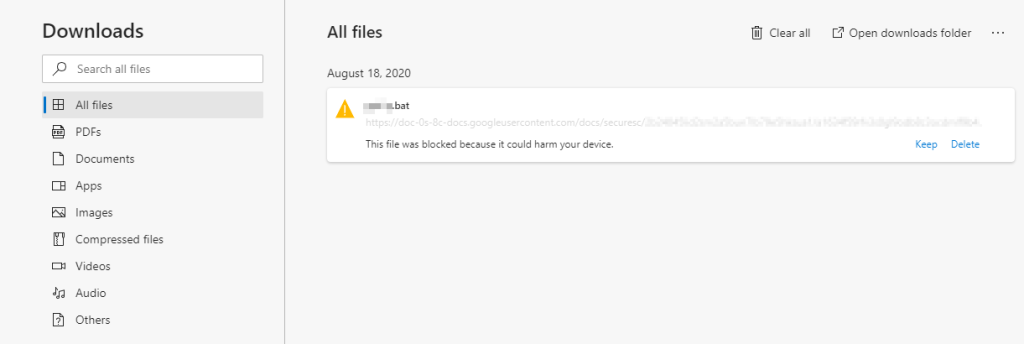
7. Use customize installation
If you want to install freeware, make sure every install message you have read. Sometimes freeware will install their other software in default that you don’t need, so the best way is using customize installation.
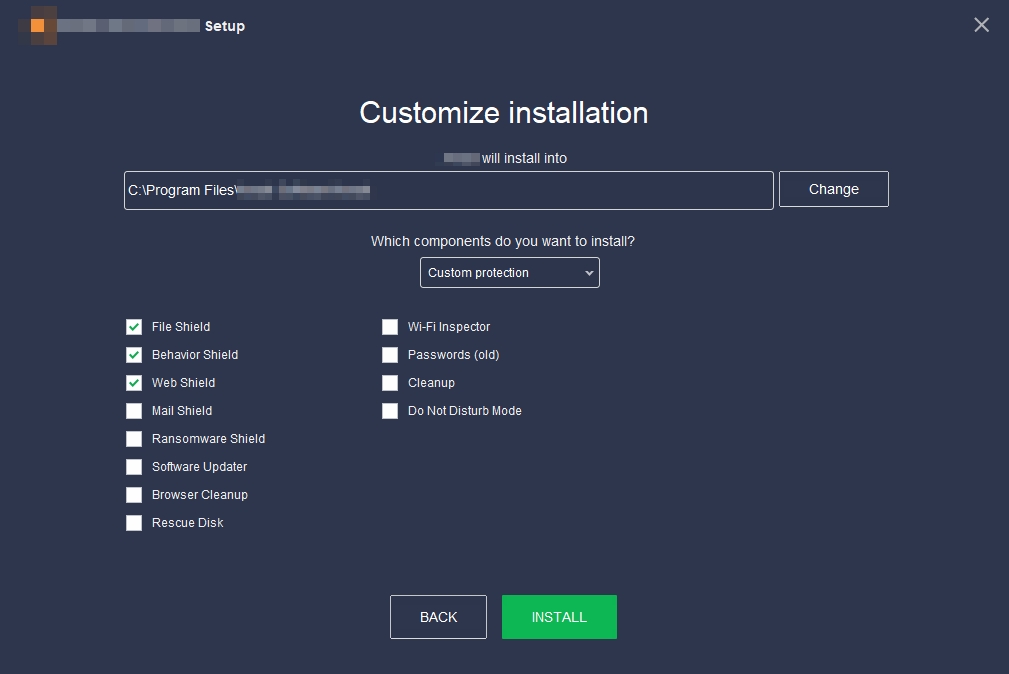
In customize installation, you can choose the components/software you want to install.
8. Don’t click on strange links/files
The phishing attack could be a pretend mail such as business email, delivery notification email, or system notification email.
Do not downloading the attachment, or clicking the link to a website that may be infected with malware.

Beware the mail with a strange attachment.

The mail pretend other brands.

Some scam emails lied that they hacked into your computer and recorded you visiting adult websites. They threaten to distribute the video to your friends within hours, unless you pay into their Bitcoin account.

The best practices for information security could reduce the chance of being attacked, but viruses will become more and more powerful in the future.
So, whether it is a company or normal user, we still need to back up our files to protect our data.
